Information: Since the configuration of SAML is based on customer-specific URL and certificates, the SAML configuration can only be done after you have provided your information during the inital project, and not already while SEEBURGER initially provides the BIS system before the start of the project. |
SEEBURGER SAML process:
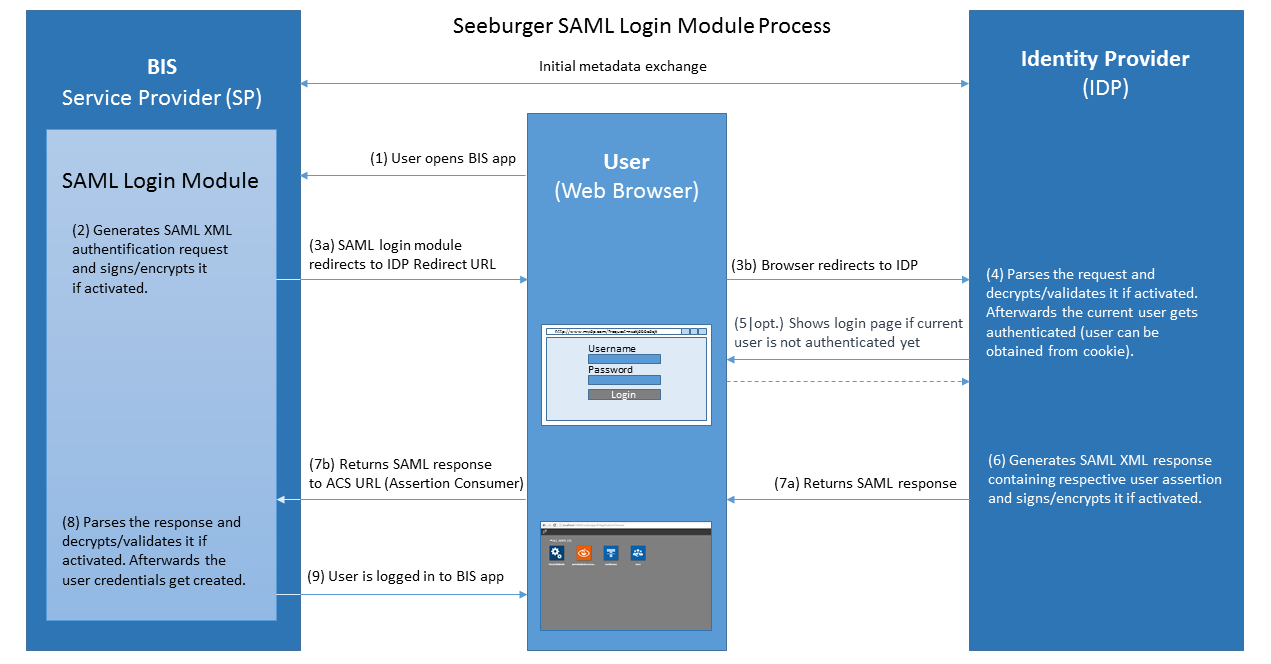
The SAML Login Module enables the single sign-on (SSO) authentication by using an external SAML Identity Provider (IDP at customer side) and acts on SAML Service Provider side (SP = SEEBURGER).
To configure SAML authentication in your identity provider (IDP), you need to enter the following information about your Service Provider (SP):
Issuer (SP)
Assertion Consumer URL (SP)
Signature Certificate
Encryption Certificate
Since this information is specific for every BIS system, it will be delivered during your initial project with SEEBURGER.
To enable SEEBURGER to configure the SAML Login Module, you need to provide the following information:
Configuration of: |
Value: |
Your URL (IDP): |
The URL of your IDP. After the authentication request is created and executed by the Login Module, the browser redirects the user to this URL (see step 2/3 of the SAML process). |
Signature Certificate: |
We recommend to use an SHA-2 algorithm to meet the highest security standards. |
Encryption Certificate: |
We recommend to use AES-256 to meet the highest security standards. |
Assertion Attributes: |
After the Login Module has retrieved, extracted and verified the authentication assertion from the IDP (see step 8 of the SAML process), the respective attributes within the assertion are used to create the required user credentials. |
Use Subject For User Credential: |
Activated/Deactivated. If activated, the Login Module extracts the name of the user from the assertion subject NameID. |
User: |
This information is required if "Use Subject For User Credential" is deactivated. If "Use Subject For User Credential" is deactivated, the authenticated user is extracted as normal assertion attribute by the name which can be defined by setting this User attribute. |
First Name: |
This information is optional. |
Last Name: |
This information is optional. |
Full Name: |
This information is optional. |
Language: |
This information is optional. |
Phone Number: |
This information is optional. |
Department: |
This information is optional. |
Note: There is no AuthnRequest sent from service provider (SP) to identity provider (IDP) for IDP initiated log-in, so make sure this is disabled on your IDP. |